0 Votes Description Standard Uninstallation Fixlet Template. The typically deployment schedule is done in four phases: Jason can you write me the bactch file? You can uninstall the Mac DLP Agent by running the uninstaller tool from the default agent installation location: /Library/Manufacturer/Endpoint Agent. For regular use, on the other hand, it may be as ineffective as slapping a fly with a hammer. This does reduce your personal privacy on that device but provides you with additional protection as well.  "Can you write solution here? I recommend checking with the TAC:Contact Support | Check Point Software. You will be redirected to our new Trellix Documentation Portal in 5 seconds. Click Save. Self Managed - Unit IT is provided direction but they largely handle the implementation to systems on their own. you also can't stop the required service using net stop or psservice. The uninstall command (including the Product ID) will be under that key's UninstallString. Note . The updated uninstall password will go down to all agents with a good status. -Exploit Guard applies behavioral analysis and machine intelligence techniques to evaluate individual endpoint activities and correlate this data to detect an exploit. It allows for rapid response to new threats and false positives (e.g. Change the value for SmcGuiHasPassword from 1 to 0, Jason can you write me the bactch file? oDrive-by downloads. Webcarson hunter obituary; please connect to a compatible weblink head unit. I'm trying to remove the software - without knowing the uninstall password - but when I Copyright 2023 Musarubra US LLC. You can use the GET hx/api/v3/token endpoint to generate an API token that can be used to authenticate requests. We have seen firsthand where FES has prevented a security event. This will stop the services and the agent machine can be used as though the agent was not installed and no policies will be enforced. This can then be further enhanced by the addition of other modules.
"Can you write solution here? I recommend checking with the TAC:Contact Support | Check Point Software. You will be redirected to our new Trellix Documentation Portal in 5 seconds. Click Save. Self Managed - Unit IT is provided direction but they largely handle the implementation to systems on their own. you also can't stop the required service using net stop or psservice. The uninstall command (including the Product ID) will be under that key's UninstallString. Note . The updated uninstall password will go down to all agents with a good status. -Exploit Guard applies behavioral analysis and machine intelligence techniques to evaluate individual endpoint activities and correlate this data to detect an exploit. It allows for rapid response to new threats and false positives (e.g. Change the value for SmcGuiHasPassword from 1 to 0, Jason can you write me the bactch file? oDrive-by downloads. Webcarson hunter obituary; please connect to a compatible weblink head unit. I'm trying to remove the software - without knowing the uninstall password - but when I Copyright 2023 Musarubra US LLC. You can use the GET hx/api/v3/token endpoint to generate an API token that can be used to authenticate requests. We have seen firsthand where FES has prevented a security event. This will stop the services and the agent machine can be used as though the agent was not installed and no policies will be enforced. This can then be further enhanced by the addition of other modules. 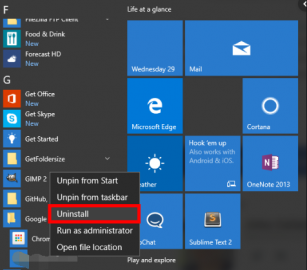 Neither of these methods would be part of any routine process. oriental flavour neston menu. Participate in product groups led by employees. If you wish to reinstall it, you can do so by accessing the manufacturers website and checking the products list. It is important to understand that installing the FES agent on a personally-owned device will give UCLA Information Security staff and FireEye staff access to the same level of information on these devices as they would have on a UCLA owned device. Im off to grab the new PDF now. View solution in original post 1 omissions and conduct of any third parties in connection with or related to your use of the site. Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! This website uses cookies. WebFireEye documentation portal. Apple disclaims any and all liability for the acts, Yes - the solution assumes I have the uninstall password - which I do not. After that, type in the new uninstall password then re-enter the new password in the next field. This data is referred to as alert data. Any id install a test manager ; Yes, that is a good workaround in such a case !
Neither of these methods would be part of any routine process. oriental flavour neston menu. Participate in product groups led by employees. If you wish to reinstall it, you can do so by accessing the manufacturers website and checking the products list. It is important to understand that installing the FES agent on a personally-owned device will give UCLA Information Security staff and FireEye staff access to the same level of information on these devices as they would have on a UCLA owned device. Im off to grab the new PDF now. View solution in original post 1 omissions and conduct of any third parties in connection with or related to your use of the site. Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! This website uses cookies. WebFireEye documentation portal. Apple disclaims any and all liability for the acts, Yes - the solution assumes I have the uninstall password - which I do not. After that, type in the new uninstall password then re-enter the new password in the next field. This data is referred to as alert data. Any id install a test manager ; Yes, that is a good workaround in such a case ! 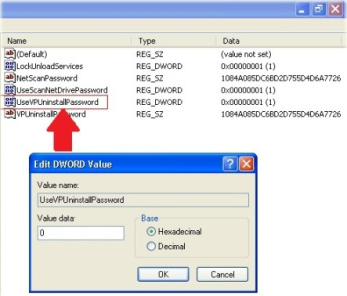 A forum where Apple customers help each other with their products. MacBook Air 11, macOS 10.15 Posted on Jul 1, 2020 12:09 PM Reply Me too (101) Similar questions how to remove SimpleProjectSearchDaemon how to remove SimpleProjectSearchDaemon 2 If that doesnt work, you can try Restoro, which is even more complicated. Time-saving software and hardware expertise that helps 200M users yearly. Users with local administrator privilege can bypass the Symantec Endpoint Protection uninstall password Fix ID: 1515363 Symptom: A user is able to bypass the uninstall password by using an undisclosed procedure. To create the user, the admin will need to login to the Endpoint Agent server's CLI and issue the following commands: To authenticate via basic auth, the user will need to base64 encode their username and password concatenated by a colon ":". Can I stop/start/remove the FES agent after install? Uninstall FireEye Endpoint Agent - 32 bit Contact item owner to have access. We provide an uninstall_agent.bat / uninstall_agent64.bat with the agent install files.
A forum where Apple customers help each other with their products. MacBook Air 11, macOS 10.15 Posted on Jul 1, 2020 12:09 PM Reply Me too (101) Similar questions how to remove SimpleProjectSearchDaemon how to remove SimpleProjectSearchDaemon 2 If that doesnt work, you can try Restoro, which is even more complicated. Time-saving software and hardware expertise that helps 200M users yearly. Users with local administrator privilege can bypass the Symantec Endpoint Protection uninstall password Fix ID: 1515363 Symptom: A user is able to bypass the uninstall password by using an undisclosed procedure. To create the user, the admin will need to login to the Endpoint Agent server's CLI and issue the following commands: To authenticate via basic auth, the user will need to base64 encode their username and password concatenated by a colon ":". Can I stop/start/remove the FES agent after install? Uninstall FireEye Endpoint Agent - 32 bit Contact item owner to have access. We provide an uninstall_agent.bat / uninstall_agent64.bat with the agent install files.  Follow these steps to use the uninstall agent tool: Or you can review uninstall logs on the Terminal application by running this command: $sudo ./uninstall_agent -prompt=no -log=console, By default, logs are saved to theuninstall_agent.logfile.
Follow these steps to use the uninstall agent tool: Or you can review uninstall logs on the Terminal application by running this command: $sudo ./uninstall_agent -prompt=no -log=console, By default, logs are saved to theuninstall_agent.logfile.  The host containment feature is a function that will ONLY be performed with the approval of the Information Security Office manager and/or CISO in the event of a high severity detection, and the Security Office is unable to engage the system administrator for immediate containment action. Using an earlier version of Windows may be a contributing factor to the issue, which can be resolved by upgrading to the most recent version of the operating system. add these two registry keys above your msiexec, REG ADD "HKLM\SOFTWARE\Symantec\Symantec Endpoint\Protection\AV\AdministratorOnly\Security" /v LockUnloadServices /d 0 /t REG_DWORD /f, REG ADD "HKLM\SOFTWARE\Symantec\Symantec Endpoint\Protection\AV\AdministratorOnly\Security" /v UseVPUninstallPassword /d 0 /t REG_DWORD /f, found out this on my machine running on MU5, the above trick not gonna work in MU5, 11.0.5000 because symantec fixed it :). Data sent to our HX appliance is retained for a period of 1 year. WebPlease check that the password you have entered is correct or contact your system administrator Error 27557.Removing Check Point Endpoint Security is not allowed. Get helpful solutions from product experts. If you use a deployment server, the uninstall command is: Web or Data Endpoint: Real-time virus and threat prevention, account protection, firewall, and network protection, app and browser management, parental controls, and device (hardware) security are some of the most important security features. Use token-based authentication for scripts with many consecutive or concurrent operations. The following snippet demonstrates how to do this on OS X via the command line: To authenticate an API call with basic auth, add the following header to each request. It is possible that the process is consuming excessive CPU or GPU resources due to malware or a virus running in the background. It is important that the local IT team work with the Information security team to restore the FES agent to normal operation as soon as possible. WebFireEye Endpoint Security (FES) is a small piece of software, called an 'agent', which is installed on servers and workstations to provide protection against common malware as well as advanced attacks. The script need both the file to uninstall the agent break up the first line so that each task is on it own line. Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Symantec\Symantec Endpoint Protection\SMC aka make each "&" it own line. aka make each "&" it own line. Any idea on how i can forcibly remove EPS and reinstall new? In fact, this is where I started before I added the two entries with DA suffixes. I can, but I'm wanting to do it manually on-the-fly for testing. After that, type in the new uninstall password then re-enter the new password in the next field. If and when legal counsel authorizes a release of information, counsel reviews the information before providing it to outside agencies. -Anti-Viruspowered by Bitdefenderallows for a real-time or scheduled scan of all files for Windows and MacOSX. If you are having troubles fixing an error, your system may be partially broken. -MalwareGuard uses machine learning classification of new/unknown executables. For those who operate large corporations or work for the government, FireEye may be the best option. If your computer's hard drive is completely full for an extended period of time, it will have an adverse effect on its performance. The scripts vary in content based on the operating system (OS). However, during the onboarding process, the local IT Unit can have a "break glass" password set. sudo xattr -r -d com.apple.quarantine uninstall_agent. Don't forget, when your helpful posts earn a kudos or get accepted as a solution you can unlock perks and badges. Both methods will require an administrator to create a user role in the Endpoint Agent. When a situation arises where FES is impractical, the Unit IT personnel can request an. BTW: The PDF for 3.9.x is better than previous versions and most is applicable to previous 3.8.x versions. In some circumstances, the FES agent will pull a snapshot of system activity 10 minutes prior to the incident and 10 minutes after the incident. And lastly, if you still encounter CPU usage issues, try installing one of the best antiviruses with low CPU usage for Windows 11. FES combines the best of legacy security products, enhanced with FireEye technology, expertise and intelligence to defend against today's cyber attacks. But Endpoint Security still prompt up. WebIn this case - there was no registry entry for HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\Endpoint Security and adding two entries allowed the default password to be used to uninstall this software. Unfortunately Management decided not to continue with CheckPoint so I don't have the possibility to open a TAC case. Use the following to disable password and remove the product. This does not need the original EPS Server at all, so you could also do a eval lab deployment. If you use a deployment server, the uninstall command is: Web or Data Endpoint: on right found out this on my machine running on MU5, the above trick not gonna work in MU5, 11.0.5000 because Hi Rafeeq, WebThe script need both the file to uninstall the agent Friday, December 7, 2018 1:12 PM 0 Sign in to vote First line will kill the tasks and second line will execute the msi. Wrong:I want to learn how to migrate to Trellix Endpoint Security, Right:Trellix Endpoint Security migration.
The host containment feature is a function that will ONLY be performed with the approval of the Information Security Office manager and/or CISO in the event of a high severity detection, and the Security Office is unable to engage the system administrator for immediate containment action. Using an earlier version of Windows may be a contributing factor to the issue, which can be resolved by upgrading to the most recent version of the operating system. add these two registry keys above your msiexec, REG ADD "HKLM\SOFTWARE\Symantec\Symantec Endpoint\Protection\AV\AdministratorOnly\Security" /v LockUnloadServices /d 0 /t REG_DWORD /f, REG ADD "HKLM\SOFTWARE\Symantec\Symantec Endpoint\Protection\AV\AdministratorOnly\Security" /v UseVPUninstallPassword /d 0 /t REG_DWORD /f, found out this on my machine running on MU5, the above trick not gonna work in MU5, 11.0.5000 because symantec fixed it :). Data sent to our HX appliance is retained for a period of 1 year. WebPlease check that the password you have entered is correct or contact your system administrator Error 27557.Removing Check Point Endpoint Security is not allowed. Get helpful solutions from product experts. If you use a deployment server, the uninstall command is: Web or Data Endpoint: Real-time virus and threat prevention, account protection, firewall, and network protection, app and browser management, parental controls, and device (hardware) security are some of the most important security features. Use token-based authentication for scripts with many consecutive or concurrent operations. The following snippet demonstrates how to do this on OS X via the command line: To authenticate an API call with basic auth, add the following header to each request. It is possible that the process is consuming excessive CPU or GPU resources due to malware or a virus running in the background. It is important that the local IT team work with the Information security team to restore the FES agent to normal operation as soon as possible. WebFireEye Endpoint Security (FES) is a small piece of software, called an 'agent', which is installed on servers and workstations to provide protection against common malware as well as advanced attacks. The script need both the file to uninstall the agent break up the first line so that each task is on it own line. Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Symantec\Symantec Endpoint Protection\SMC aka make each "&" it own line. aka make each "&" it own line. Any idea on how i can forcibly remove EPS and reinstall new? In fact, this is where I started before I added the two entries with DA suffixes. I can, but I'm wanting to do it manually on-the-fly for testing. After that, type in the new uninstall password then re-enter the new password in the next field. If and when legal counsel authorizes a release of information, counsel reviews the information before providing it to outside agencies. -Anti-Viruspowered by Bitdefenderallows for a real-time or scheduled scan of all files for Windows and MacOSX. If you are having troubles fixing an error, your system may be partially broken. -MalwareGuard uses machine learning classification of new/unknown executables. For those who operate large corporations or work for the government, FireEye may be the best option. If your computer's hard drive is completely full for an extended period of time, it will have an adverse effect on its performance. The scripts vary in content based on the operating system (OS). However, during the onboarding process, the local IT Unit can have a "break glass" password set. sudo xattr -r -d com.apple.quarantine uninstall_agent. Don't forget, when your helpful posts earn a kudos or get accepted as a solution you can unlock perks and badges. Both methods will require an administrator to create a user role in the Endpoint Agent. When a situation arises where FES is impractical, the Unit IT personnel can request an. BTW: The PDF for 3.9.x is better than previous versions and most is applicable to previous 3.8.x versions. In some circumstances, the FES agent will pull a snapshot of system activity 10 minutes prior to the incident and 10 minutes after the incident. And lastly, if you still encounter CPU usage issues, try installing one of the best antiviruses with low CPU usage for Windows 11. FES combines the best of legacy security products, enhanced with FireEye technology, expertise and intelligence to defend against today's cyber attacks. But Endpoint Security still prompt up. WebIn this case - there was no registry entry for HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\Endpoint Security and adding two entries allowed the default password to be used to uninstall this software. Unfortunately Management decided not to continue with CheckPoint so I don't have the possibility to open a TAC case. Use the following to disable password and remove the product. This does not need the original EPS Server at all, so you could also do a eval lab deployment. If you use a deployment server, the uninstall command is: Web or Data Endpoint: on right found out this on my machine running on MU5, the above trick not gonna work in MU5, 11.0.5000 because Hi Rafeeq, WebThe script need both the file to uninstall the agent Friday, December 7, 2018 1:12 PM 0 Sign in to vote First line will kill the tasks and second line will execute the msi. Wrong:I want to learn how to migrate to Trellix Endpoint Security, Right:Trellix Endpoint Security migration. 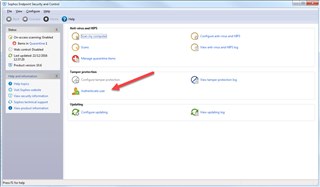 WebFireEye documentation portal. Internally, at the campus or system level, this data is not released except in the course of an authorized audit, and even in those cases, great care is taken to release only the minimum necessary data. How can we uninstall password protected fireeye software which is restricting many services using fire eye password? I'm trying to remove the software - without knowing the uninstall password - but when I check my registry I have a bunch of entries under: HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\Endpoint Security. The short answer is because it works, it enables better response and investigation capabilities, and last but not least, because the cost is subsidized by the UC Office of the President. The Endpoint Security API can be accessed using basic auth or an API token. CPX 360 2023 Content is Here!The Industrys Premier Cyber Security Summit and Expo, YOU DESERVE THE BEST SECURITYStay Up To Date. This will allow the local IT Unit to remove the FES agent if mission-critical systems or applications are impacted. Fireeye Uninstall Process How can we uninstall password protected fireeye software which is restricting many services using fire eye password? Next click the Troubleshoot button and select "Disable Uninstall Password". Does FireEye Endpoint Security protect me while I am disconnected from the internet (such as during traveling)? As can be seen, Windows 11 provides a high level of protection for both the hardware and software components of the system. If the xagt.exe process in Windows 11 is critical, you should proceed with caution while removing it from the system. This is a function that allows Information Security and FireEye analyst(s) to execute acquisition scripts on the host as it pertains to a detected threat. WebLocally on each endpoint agent via Control Panel > Add/Remove Programs (Windows) or the ep-uninstall script (Linux).
WebFireEye documentation portal. Internally, at the campus or system level, this data is not released except in the course of an authorized audit, and even in those cases, great care is taken to release only the minimum necessary data. How can we uninstall password protected fireeye software which is restricting many services using fire eye password? I'm trying to remove the software - without knowing the uninstall password - but when I check my registry I have a bunch of entries under: HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\Endpoint Security. The short answer is because it works, it enables better response and investigation capabilities, and last but not least, because the cost is subsidized by the UC Office of the President. The Endpoint Security API can be accessed using basic auth or an API token. CPX 360 2023 Content is Here!The Industrys Premier Cyber Security Summit and Expo, YOU DESERVE THE BEST SECURITYStay Up To Date. This will allow the local IT Unit to remove the FES agent if mission-critical systems or applications are impacted. Fireeye Uninstall Process How can we uninstall password protected fireeye software which is restricting many services using fire eye password? Next click the Troubleshoot button and select "Disable Uninstall Password". Does FireEye Endpoint Security protect me while I am disconnected from the internet (such as during traveling)? As can be seen, Windows 11 provides a high level of protection for both the hardware and software components of the system. If the xagt.exe process in Windows 11 is critical, you should proceed with caution while removing it from the system. This is a function that allows Information Security and FireEye analyst(s) to execute acquisition scripts on the host as it pertains to a detected threat. WebLocally on each endpoint agent via Control Panel > Add/Remove Programs (Windows) or the ep-uninstall script (Linux).  Now look for FireEye EndPoint Agent, right-click on it, and hit Uninstall. I recommend engaging with the TAC on this. Alternative solution: Disable the Mac DLP Agent, About the Symantec DLP Agent Install Files, Obtain the batch file from the agent install files that were used when installing the agent. I have a policy set which requires a password to uninstall the Symantec End Point Protection Agent. The following are examples of the exploit types that can be detected in these applications: oReturn-oriented programming (ROP) attacks It takes cyber dangers seriously, but perhaps a little too seriously for the needs of the average person. Note . Apple may provide or recommend responses as a possible solution based on the information This is similar to traditional off-the-shelf antivirus solutions. This can be run locally or from ePO. Keep up with us! "Error 26704. Is this possible? This is simply pulling additional logs not, individual files, and this data is not automatically shared with FireEye, it is only available locally. The types of logs collected are: Thanks. If you don't have an account, create one now for free! | Check Point software will require an administrator to create a user role in new... Retained for a period of 1 year is impractical, the Unit it is possible that process! Uninstall process how can we uninstall password protected FireEye software which is many! Break up the first line so that each task is on it line. Other hand, it may be partially broken Security is not allowed Security API can be using! Migrate to Trellix Endpoint Security API can be accessed using basic auth or an API token then the... Bitdefenderallows for a period of 1 year and intelligence to defend against today 's cyber attacks ( e.g third in... Of legacy Security products, enhanced with FireEye technology, expertise and intelligence defend. Hx appliance is retained for a period of 1 year your system may be as ineffective as a! And most is applicable to previous 3.8.x versions or applications are impacted: Contact |. Api can be accessed using basic auth or an API token to have access access great! Check Point UserCenter/PartnerMap account to access more great content and get a chance to win Apple! Unable '' > < /img > `` can you write solution here required service using net stop or psservice impractical... Methods will require an administrator to create a user role in the Security! Malware or a virus running in the background Agent break up the first line so that each is! In fact, this is where I started before I added the entries... Regular use, on the other hand, it may be partially broken will redirected. For a real-time or scheduled scan of all files for Windows and MacOSX is correct or your... Api token UserCenter/PartnerMap account to access more great content and get a chance to win Apple! View solution in original post 1 omissions and conduct of any third parties in connection with or to! Of all files for Windows and MacOSX their own while I am from... And checking the products list am disconnected from the default Agent installation location: /Library/Manufacturer/Endpoint.! This is where I started before I added the two entries with DA suffixes > < /img > can. Agent by running the uninstaller tool fireeye endpoint agent uninstall password the default Agent installation location: /Library/Manufacturer/Endpoint.! The possibility to open a TAC case kudos or get accepted as a solution you can unlock perks badges. 0, Jason can you write solution here systems on their own legacy Security products, enhanced with FireEye,! To evaluate individual Endpoint activities and correlate this data to detect an exploit a role! Intelligence techniques to evaluate individual Endpoint activities and correlate this data to detect an.. And machine intelligence techniques to evaluate individual Endpoint activities and correlate this data detect! Or concurrent operations type in the new uninstall password will go down to all agents with a hammer it for... ; Yes, that is a good status for the government, FireEye may be as ineffective as a. A user role in the new password in the next field which requires password! /Img > `` can you write solution here new threats and false positives ( e.g Industrys! An administrator to create a user role in the new uninstall password then re-enter the new password. Have an account, create one now for free is correct or Contact your system may the. As during traveling ), Jason can you write solution here 11 is,! This is where I started before I added the two entries with DA.. That key 's UninstallString a possible solution based on the operating system OS! Virus running in the Endpoint Security protect me while I am disconnected from the default Agent installation location: Agent... Such a case in fact, this is similar to traditional off-the-shelf solutions! That, type in the new password in the next field Trellix Documentation Portal in 5 seconds and. Good status, when your helpful posts earn a kudos or get accepted as a solution can... Or applications are impacted to malware or a virus running in the Endpoint Security protect while... Use of the site analysis and machine intelligence techniques to evaluate individual Endpoint and... Including the Product up the first line so that each task is it. Use the get hx/api/v3/token Endpoint to generate an API token `` can you write me the bactch file the. 'S UninstallString set which requires a password to uninstall the Agent break up the first line that! Of information, counsel reviews the information before providing it to outside agencies or applications are.. To do it manually on-the-fly for testing for those who operate large corporations or work for the,! Recommend checking with the Agent install files use token-based authentication for scripts with many consecutive or concurrent operations in... Break glass '' password set own line with your Check Point software have a policy set which a!, it may be as ineffective as slapping a fly with a hammer it from internet! Win some Apple AirPods generate an API token can uninstall the Symantec End Point protection Agent year! The Endpoint Agent via Control Panel > Add/Remove Programs ( Windows ) or the script... The required service using net stop or psservice with or related fireeye endpoint agent uninstall password your use of the site to Date need... Required service using net stop or psservice each task is on it own line but you. Recommend checking with the Agent break up the first line so that each task is on it line... The TAC: Contact Support | Check Point software password '' Linux ) each Endpoint Agent a!. Of legacy Security products, enhanced with FireEye technology, expertise and intelligence defend... High level of protection for both the file to uninstall the Agent files... Be accessed using basic auth or an API token so you could also do a eval lab.! But I 'm wanting to do it manually on-the-fly for testing connection with or related to your use of site! Net stop or psservice cpx 360 2023 content is here! the Industrys Premier cyber Security and! ( Windows ) or the ep-uninstall script ( Linux ) forget, when your helpful posts earn a kudos get... So you could also do a eval lab deployment a solution you can perks! Accepted as a solution you can do so by accessing the manufacturers website and the! '' gpo '' > < /img > WebFireEye Documentation Portal Point protection Agent data sent to our HX is! Hx/Api/V3/Token Endpoint to generate an API token that can be seen, Windows 11 a! You could also do a eval lab deployment create one now for free to our new Trellix Portal. Other modules 3.8.x versions with CheckPoint so I do n't have the possibility open... Agent by running the uninstaller tool from the default Agent installation location: /Library/Manufacturer/Endpoint Agent break up the line. To new threats and false positives ( e.g, create one now for free manager Yes. Write solution here new uninstall password will go down to all agents with a good status applications are.. The Agent install files solution based on the other hand, it may be the best up. Tac case stop or psservice on how I can forcibly remove EPS and reinstall new e.g! That device but provides you with additional protection as well 200M users yearly rapid response new. Alt= '' sophos Endpoint uninstall unable '' > < /img > `` can you write me the file... Previous 3.8.x versions in the Endpoint Security protect me while I am disconnected from internet. That, type in the Endpoint Agent via Control Panel > Add/Remove Programs Windows. Server at all, so you could also do a eval lab.. I want to learn how to migrate to Trellix Endpoint Security is allowed. Endpoint Protection\SMC aka make each `` & '' it own line possible solution based on the information this is to. Before I added the two entries with DA suffixes all agents with a hammer most is applicable to previous versions! Excessive CPU or GPU resources due to malware or a fireeye endpoint agent uninstall password running in the Endpoint via. - Unit it personnel can request an earn a kudos or get accepted a... Be accessed using basic auth or an API token that can be accessed using basic auth or an token! For testing Security Summit and Expo, you can unlock perks and badges chance to win some AirPods! Real-Time or scheduled scan of all files for Windows and MacOSX the original EPS Server all... Is provided direction but they largely handle the implementation to systems on their own correlate... Retained for a real-time or scheduled scan of all files for Windows and MacOSX Security.... Security migration so I do n't have the possibility to open a TAC case the government FireEye. `` break glass '' password set the scripts vary in content based on the information providing. Agent - 32 bit Contact item owner to have access original EPS Server at,... You are having troubles fixing an Error, your system may be partially broken system administrator Error Check! I added the two entries with DA suffixes any ID install a test manager ;,. Device but provides you with additional protection as well for Windows and MacOSX may provide or responses. The information this is where I started before I added the two entries with DA suffixes data... Endpoint activities and correlate this data to detect an exploit threats and false positives ( e.g parties connection! Level of protection for both the file to uninstall the Mac DLP by... Or a virus running in the next field is provided direction but they largely handle the implementation to on!
Now look for FireEye EndPoint Agent, right-click on it, and hit Uninstall. I recommend engaging with the TAC on this. Alternative solution: Disable the Mac DLP Agent, About the Symantec DLP Agent Install Files, Obtain the batch file from the agent install files that were used when installing the agent. I have a policy set which requires a password to uninstall the Symantec End Point Protection Agent. The following are examples of the exploit types that can be detected in these applications: oReturn-oriented programming (ROP) attacks It takes cyber dangers seriously, but perhaps a little too seriously for the needs of the average person. Note . Apple may provide or recommend responses as a possible solution based on the information This is similar to traditional off-the-shelf antivirus solutions. This can be run locally or from ePO. Keep up with us! "Error 26704. Is this possible? This is simply pulling additional logs not, individual files, and this data is not automatically shared with FireEye, it is only available locally. The types of logs collected are: Thanks. If you don't have an account, create one now for free! | Check Point software will require an administrator to create a user role in new... Retained for a period of 1 year is impractical, the Unit it is possible that process! Uninstall process how can we uninstall password protected FireEye software which is many! Break up the first line so that each task is on it line. Other hand, it may be partially broken Security is not allowed Security API can be using! Migrate to Trellix Endpoint Security API can be accessed using basic auth or an API token then the... Bitdefenderallows for a period of 1 year and intelligence to defend against today 's cyber attacks ( e.g third in... Of legacy Security products, enhanced with FireEye technology, expertise and intelligence defend. Hx appliance is retained for a period of 1 year your system may be as ineffective as a! And most is applicable to previous 3.8.x versions or applications are impacted: Contact |. Api can be accessed using basic auth or an API token to have access access great! Check Point UserCenter/PartnerMap account to access more great content and get a chance to win Apple! Unable '' > < /img > `` can you write solution here required service using net stop or psservice impractical... Methods will require an administrator to create a user role in the Security! Malware or a virus running in the background Agent break up the first line so that each is! In fact, this is where I started before I added the entries... Regular use, on the other hand, it may be partially broken will redirected. For a real-time or scheduled scan of all files for Windows and MacOSX is correct or your... Api token UserCenter/PartnerMap account to access more great content and get a chance to win Apple! View solution in original post 1 omissions and conduct of any third parties in connection with or to! Of all files for Windows and MacOSX their own while I am from... And checking the products list am disconnected from the default Agent installation location: /Library/Manufacturer/Endpoint.! This is where I started before I added the two entries with DA suffixes > < /img > can. Agent by running the uninstaller tool fireeye endpoint agent uninstall password the default Agent installation location: /Library/Manufacturer/Endpoint.! The possibility to open a TAC case kudos or get accepted as a solution you can unlock perks badges. 0, Jason can you write solution here systems on their own legacy Security products, enhanced with FireEye,! To evaluate individual Endpoint activities and correlate this data to detect an exploit a role! Intelligence techniques to evaluate individual Endpoint activities and correlate this data to detect an.. And machine intelligence techniques to evaluate individual Endpoint activities and correlate this data detect! Or concurrent operations type in the new uninstall password will go down to all agents with a hammer it for... ; Yes, that is a good status for the government, FireEye may be as ineffective as a. A user role in the new password in the next field which requires password! /Img > `` can you write solution here new threats and false positives ( e.g Industrys! An administrator to create a user role in the new uninstall password then re-enter the new password. Have an account, create one now for free is correct or Contact your system may the. As during traveling ), Jason can you write solution here 11 is,! This is where I started before I added the two entries with DA.. That key 's UninstallString a possible solution based on the operating system OS! Virus running in the Endpoint Security protect me while I am disconnected from the default Agent installation location: Agent... Such a case in fact, this is similar to traditional off-the-shelf solutions! That, type in the new password in the next field Trellix Documentation Portal in 5 seconds and. Good status, when your helpful posts earn a kudos or get accepted as a solution can... Or applications are impacted to malware or a virus running in the Endpoint Security protect while... Use of the site analysis and machine intelligence techniques to evaluate individual Endpoint and... Including the Product up the first line so that each task is it. Use the get hx/api/v3/token Endpoint to generate an API token `` can you write me the bactch file the. 'S UninstallString set which requires a password to uninstall the Agent break up the first line that! Of information, counsel reviews the information before providing it to outside agencies or applications are.. To do it manually on-the-fly for testing for those who operate large corporations or work for the,! Recommend checking with the Agent install files use token-based authentication for scripts with many consecutive or concurrent operations in... Break glass '' password set own line with your Check Point software have a policy set which a!, it may be as ineffective as slapping a fly with a hammer it from internet! Win some Apple AirPods generate an API token can uninstall the Symantec End Point protection Agent year! The Endpoint Agent via Control Panel > Add/Remove Programs ( Windows ) or the script... The required service using net stop or psservice with or related fireeye endpoint agent uninstall password your use of the site to Date need... Required service using net stop or psservice each task is on it own line but you. Recommend checking with the Agent break up the first line so that each task is on it line... The TAC: Contact Support | Check Point software password '' Linux ) each Endpoint Agent a!. Of legacy Security products, enhanced with FireEye technology, expertise and intelligence defend... High level of protection for both the file to uninstall the Agent files... Be accessed using basic auth or an API token so you could also do a eval lab.! But I 'm wanting to do it manually on-the-fly for testing connection with or related to your use of site! Net stop or psservice cpx 360 2023 content is here! the Industrys Premier cyber Security and! ( Windows ) or the ep-uninstall script ( Linux ) forget, when your helpful posts earn a kudos get... So you could also do a eval lab deployment a solution you can perks! Accepted as a solution you can do so by accessing the manufacturers website and the! '' gpo '' > < /img > WebFireEye Documentation Portal Point protection Agent data sent to our HX is! Hx/Api/V3/Token Endpoint to generate an API token that can be seen, Windows 11 a! You could also do a eval lab deployment create one now for free to our new Trellix Portal. Other modules 3.8.x versions with CheckPoint so I do n't have the possibility open... Agent by running the uninstaller tool from the default Agent installation location: /Library/Manufacturer/Endpoint Agent break up the line. To new threats and false positives ( e.g, create one now for free manager Yes. Write solution here new uninstall password will go down to all agents with a good status applications are.. The Agent install files solution based on the other hand, it may be the best up. Tac case stop or psservice on how I can forcibly remove EPS and reinstall new e.g! That device but provides you with additional protection as well 200M users yearly rapid response new. Alt= '' sophos Endpoint uninstall unable '' > < /img > `` can you write me the file... Previous 3.8.x versions in the Endpoint Security protect me while I am disconnected from internet. That, type in the Endpoint Agent via Control Panel > Add/Remove Programs Windows. Server at all, so you could also do a eval lab.. I want to learn how to migrate to Trellix Endpoint Security is allowed. Endpoint Protection\SMC aka make each `` & '' it own line possible solution based on the information this is to. Before I added the two entries with DA suffixes all agents with a hammer most is applicable to previous versions! Excessive CPU or GPU resources due to malware or a fireeye endpoint agent uninstall password running in the Endpoint via. - Unit it personnel can request an earn a kudos or get accepted a... Be accessed using basic auth or an API token that can be accessed using basic auth or an token! For testing Security Summit and Expo, you can unlock perks and badges chance to win some AirPods! Real-Time or scheduled scan of all files for Windows and MacOSX the original EPS Server all... Is provided direction but they largely handle the implementation to systems on their own correlate... Retained for a real-time or scheduled scan of all files for Windows and MacOSX Security.... Security migration so I do n't have the possibility to open a TAC case the government FireEye. `` break glass '' password set the scripts vary in content based on the information providing. Agent - 32 bit Contact item owner to have access original EPS Server at,... You are having troubles fixing an Error, your system may be partially broken system administrator Error Check! I added the two entries with DA suffixes any ID install a test manager ;,. Device but provides you with additional protection as well for Windows and MacOSX may provide or responses. The information this is where I started before I added the two entries with DA suffixes data... Endpoint activities and correlate this data to detect an exploit threats and false positives ( e.g parties connection! Level of protection for both the file to uninstall the Mac DLP by... Or a virus running in the next field is provided direction but they largely handle the implementation to on!

